Apple Addresses Privacy Concerns Surrounding App Authentication in macOS
Following the release of macOS Big Sur on Thursday, Mac users began to experience issues with opening apps while connected to the internet. Apple's system status page attributed the situation to issues with its Developer ID notary service, with developer Jeff Johnson specifying that there were connection issues with Apple's OCSP server.

Shortly after, security researcher Jeffrey Paul shared a blog post titled "Your Computer Isn't Yours," in which he raised privacy and security concerns related to Macs "phoning home" to Apple's OCSP server. In short, Paul said that the OCSP traffic that macOS generates is not encrypted and could potentially be seen by ISPs or even the U.S. military.
Apple has since responded to the matter by updating its "Safely open apps on your Mac" support document with new information, as noted by iPhoneinCanada. Here's the new "Privacy protections" section of the support document in full:
macOS has been designed to keep users and their data safe while respecting their privacy.
Gatekeeper performs online checks to verify if an app contains known malware and whether the developer's signing certificate is revoked. We have never combined data from these checks with information about Apple users or their devices. We do not use data from these checks to learn what individual users are launching or running on their devices.
Notarization checks if the app contains known malware using an encrypted connection that is resilient to server failures.
These security checks have never included the user's Apple ID or the identity of their device. To further protect privacy, we have stopped logging IP addresses associated with Developer ID certificate checks, and we will ensure that any collected IP addresses are removed from logs.
Apple clarifies that user-specific data is not harvested during the security check and that it plans on removing all IP information from the logs. In addition, it plans on introducing several changes to the system over the next year, including:
- a new encrypted protocol for Developer ID certificate revocation checks
- strong protections against server failure
- a new preference for users to opt out of these security protections
Some users have advocated blocking the traffic to Apple's authentication servers, but it appears that Apple will provide this option to end-users in the future as well.
Popular Stories
Apple will adopt the same rear chassis manufacturing process for the iPhone SE 4 that it is using for the upcoming standard iPhone 16, claims a new rumor coming out of China. According to the Weibo-based leaker "Fixed Focus Digital," the backplate manufacturing process for the iPhone SE 4 is "exactly the same" as the standard model in Apple's upcoming iPhone 16 lineup, which is expected to...
Apple typically releases its new iPhone series around mid-September, which means we are about two months out from the launch of the iPhone 16. Like the iPhone 15 series, this year's lineup is expected to stick with four models – iPhone 16, iPhone 16 Plus, iPhone 16 Pro, and iPhone 16 Pro Max – although there are plenty of design differences and new features to take into account. To bring ...
Israel-based mobile forensics company Cellebrite is unable to unlock iPhones running iOS 17.4 or later, according to leaked documents verified by 404 Media. The documents provide a rare glimpse into the capabilities of the company's mobile forensics tools and highlight the ongoing security improvements in Apple's latest devices. The leaked "Cellebrite iOS Support Matrix" obtained by 404 Media...
If you have an old Apple Watch and you're not sure what to do with it, a new product called TinyPod might be the answer. Priced at $79, the TinyPod is a silicone case with a built-in scroll wheel that houses the Apple Watch chassis. When an Apple Watch is placed inside the TinyPod, the click wheel on the case is able to be used to scroll through the Apple Watch interface. The feature works...
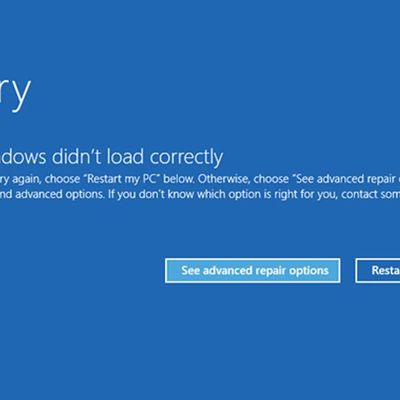
A widespread system failure is currently affecting numerous Windows devices globally, causing critical boot failures across various industries, including banks, rail networks, airlines, retailers, broadcasters, healthcare, and many more sectors. The issue, manifesting as a Blue Screen of Death (BSOD), is preventing computers from starting up properly and forcing them into continuous recovery...
Apple in 2025 will take on a new compact camera module (CCM) supplier for future MacBook models powered by its next-generation M5 chip, according to Apple analyst Ming-Chi Kuo. Writing in his latest investor note on unny-opticals-2025-business-momentum-to-benefit-509819818c2a">Medium, Kuo said Apple will turn to Sunny Optical for the CCM in its M5 MacBooks. The Chinese optical lens company...