Apple Updates Malware Definitions to Protect Against Botnet Threat Coordinated Via Reddit
Last week, Russian anti-virus firm Doctor Web disclosed a newly discovered piece of OS X malware known as Mac.BackDoor.iWorm that at the time had affected roughly 17,000 machines around the world. While the exact mechanism of infection was unclear, an interesting twist to the story involves compromised machines running search queries on Reddit to obtain instructions about which command and control servers should be used to manage the botnet.
It is worth mentioning that in order to acquire a control server address list, the bot uses the search service at reddit.com, and -- as a search query -- specifies hexadecimal values of the first 8 bytes of the MD5 hash of the current date. The reddit.com search returns a web page containing a list of botnet C&C servers and ports published by criminals in comments to the post minecraftserverlists under the account vtnhiaovyd.
Once connected to a command and control server, the backdoor opened by the malware on the user's system can receive instructions to perform a variety of tasks, from stealing sensitive information to receiving or spreading additional malware.
In an effort to address the threat, Apple has now updated its "Xprotect" anti-malware system to recognize two different variants of the iWorm malware and prevent them from being installed on users' machines.

First introduced with OS X Snow Leopard, Xprotect is a rudimentary anti-malware system that recognizes and alerts users to the presence of various types of malware. Given the relative rarity of malware targeting OS X, the malware definitions are updated infrequently, although users' machines automatically check for updates on a daily basis. Apple also uses the Xprotect system on occasion to enforce minimum version requirements for plug-ins such as Flash Player and Java, forcing users to upgrade from older versions known to carry significant security risks.
Popular Stories
Apple will adopt the same rear chassis manufacturing process for the iPhone SE 4 that it is using for the upcoming standard iPhone 16, claims a new rumor coming out of China. According to the Weibo-based leaker "Fixed Focus Digital," the backplate manufacturing process for the iPhone SE 4 is "exactly the same" as the standard model in Apple's upcoming iPhone 16 lineup, which is expected to...
Apple typically releases its new iPhone series around mid-September, which means we are about two months out from the launch of the iPhone 16. Like the iPhone 15 series, this year's lineup is expected to stick with four models – iPhone 16, iPhone 16 Plus, iPhone 16 Pro, and iPhone 16 Pro Max – although there are plenty of design differences and new features to take into account. To bring ...
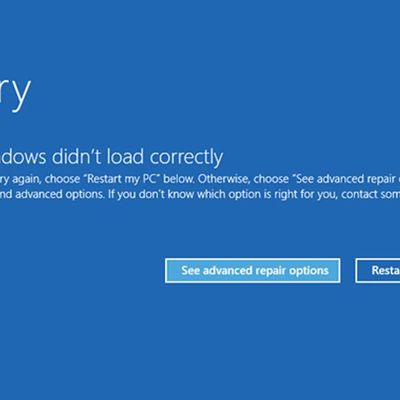
A widespread system failure is currently affecting numerous Windows devices globally, causing critical boot failures across various industries, including banks, rail networks, airlines, retailers, broadcasters, healthcare, and many more sectors. The issue, manifesting as a Blue Screen of Death (BSOD), is preventing computers from starting up properly and forcing them into continuous recovery...
Israel-based mobile forensics company Cellebrite is unable to unlock iPhones running iOS 17.4 or later, according to leaked documents verified by 404 Media. The documents provide a rare glimpse into the capabilities of the company's mobile forensics tools and highlight the ongoing security improvements in Apple's latest devices. The leaked "Cellebrite iOS Support Matrix" obtained by 404 Media...
Apple is seemingly planning a rework of the Apple Watch lineup for 2024, according to a range of reports from over the past year. Here's everything we know so far. Apple is expected to continue to offer three different Apple Watch models in five casing sizes, but the various display sizes will allegedly grow by up to 12% and the casings will get taller. Based on all of the latest rumors,...
If you have an old Apple Watch and you're not sure what to do with it, a new product called TinyPod might be the answer. Priced at $79, the TinyPod is a silicone case with a built-in scroll wheel that houses the Apple Watch chassis. When an Apple Watch is placed inside the TinyPod, the click wheel on the case is able to be used to scroll through the Apple Watch interface. The feature works...